OKTA Overview
Okta and Auth0 Platforms address the critical challenge of secure access and authentication in the digital landscape. By placing Identity at the core of business operations, these platforms enhance security and foster growth. They provide a robust solution for managing digital identities, ensuring that businesses can automate authentication processes seamlessly. This approach not only safeguards sensitive information but also streamlines user access across various applications and services. With thousands of integrations available, Okta and Auth0 cater to diverse industry needs, offering flexibility and scalability. Their focus on Identity as a foundational element empowers organizations to maintain security while supporting innovation and expansion.
Use Cases
Customers recommend Workflow Management, Helpdesk Management, Communication Management, as the business use cases that they have been most satisfied with while using OKTA.
Business Priorities
Acquire Customers and Scale Best Practices are the most popular business priorities that customers and associates have achieved using OKTA.
OKTA Use-Cases and Business Priorities: Customer Satisfaction Data
OKTA works with different mediums / channels such as Phone Calls.
OKTA's features include Dashboard, Personalization, Widgets, etc. and OKTA support capabilities include Chat Support, Email Support, Phone Support, etc. also OKTA analytics capabilities include Analytics, and Custom Reports.
Reviews
"...It s helped onboard acquisition groups faster and reduced the need for VPN...." Peer review by George Hegedus
OKTA, ClickGUARD, eSign PDF, Signable, ShippingEasy, etc., all belong to a category of solutions that help Digital Signature. Each of them excels in different abilities. Therefore, determining the best platform for your business will depend on your specific needs and requirements.
Okta's Workforce and Customer Identity Clouds enable secure access, authentication, and automation. Identity is placed at the heart of business security and growth.
Popular Business Setting
for OKTA
Top Industries
- Computer Software
- Information Technology and Services
- Internet
Popular in
- Enterprise
- Mid Market
- Large Enterprise
OKTA is popular in Computer Software, Information Technology And Services, and Internet and is widely used by Enterprise, Mid Market, and Large Enterprise.
OKTA Customer wins, Customer success stories, Case studies
How can OKTA enhance your Workflow Management process?
How efficiently Does OKTA manage your Helpdesk Management?
What Are the key features of OKTA for Communication Management?
What benefits does OKTA offer for Engagement Management?
How does OKTA facilitate Onboarding?
11 buyers and buying teams have used Cuspera to assess how well OKTA solved their Digital Signature needs. Cuspera uses 6693 insights from these buyers along with peer reviews, customer case studies, testimonials, expert blogs and vendor provided installation data to help you assess the fit for your specific Digital Signature needs.
Frequently Asked Questions(FAQ)
for OKTA
What is OKTA?
OKTA is a cloud-based identity provider that enables organizations to secure their digital interactions with employees and customers. It securely connects the right people to the right technologies at the right time. It protects the identities of their workforces and customers. It caters to businesses across various industries such as information technology (IT), consumer services, energy and utilities, telecommunications and more.
It creates secure, delightful experiences quickly by offloading customer identity management, protecting and enabling employees, contractors, and partners. Stand up authentication and user management customized and handle complexity. With more than 7,000 pre-built integrations to applications and infrastructure providers, OKTA provides simple and secure access to people and organizations everywhere, giving them the confidence to reach their full potential.
Key features include access request management, account management, compliance management, user provisioning and multi-factor authentication.
What is OKTA used for?
What are the top features of OKTA?
Who uses OKTA?
What are OKTA alternatives?
Where is OKTA located?
OKTA Competitors
OKTA Features
- Low
- Medium
- High
| FEATURE | RATINGS AND REVIEWS |
|---|---|
| AI Powered | Read Reviews (21) |
| Analytics | Read Reviews (125) |
| Custom Reports | Read Reviews (601) |
| CAPABILITIES | RATINGS AND REVIEWS |
|---|---|
| AI Powered | Read Reviews (21) |
| Analytics | Read Reviews (125) |
| Custom Reports | Read Reviews (601) |
OKTA Integrations
OKTA integrates with a wide range of software applications through its robust data import and export capabilities.
Few API Integrations for OKTA
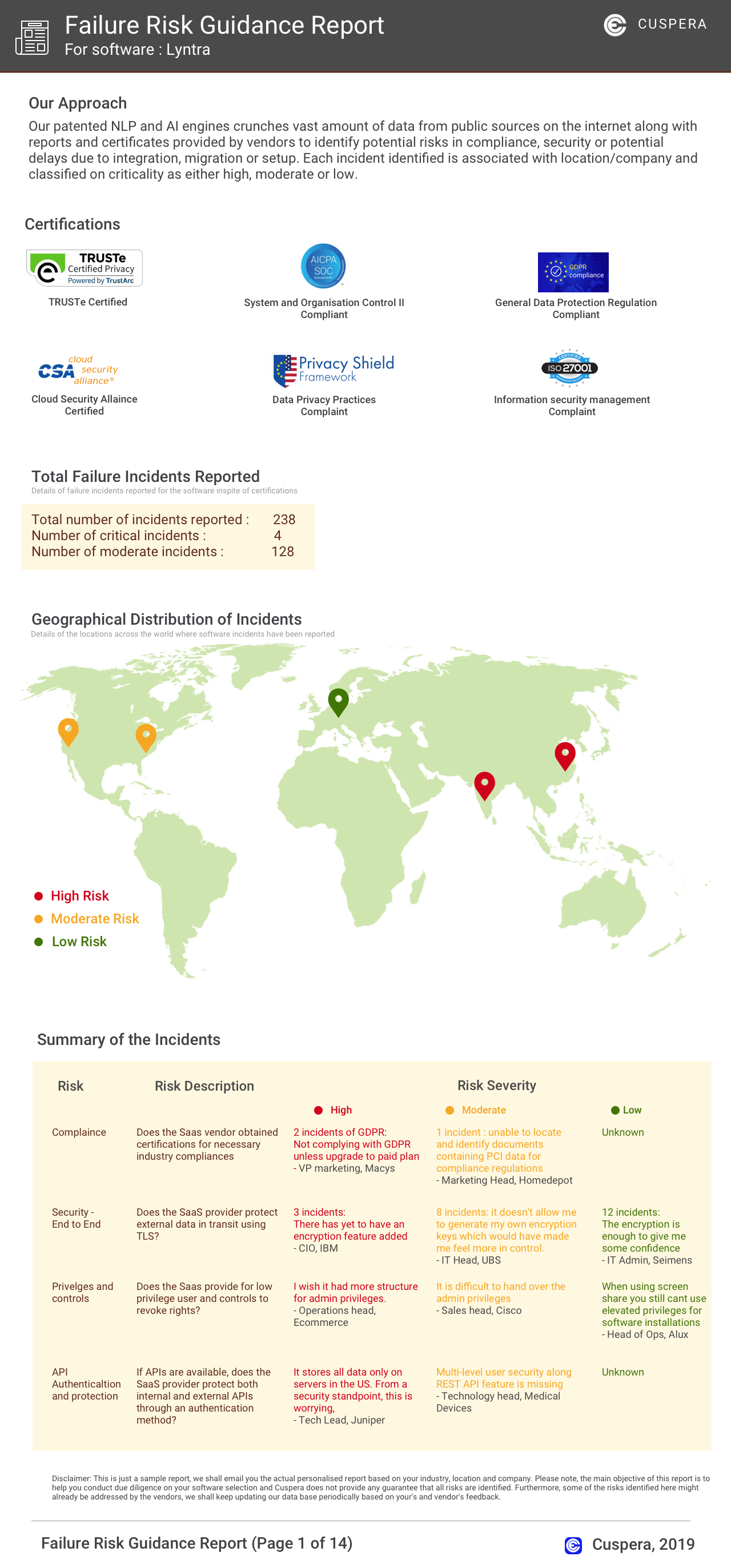
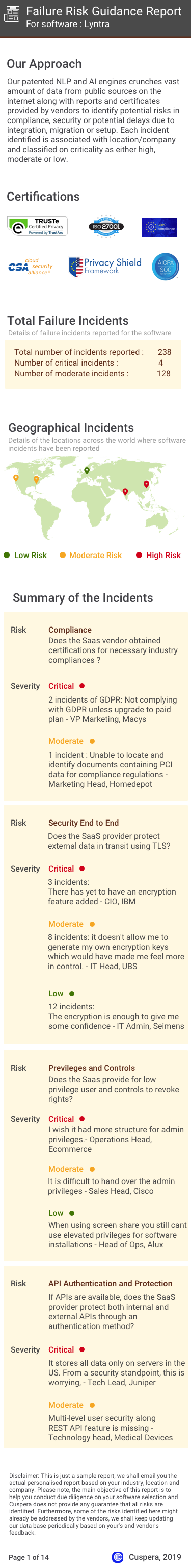
Software Failure Risk Guidance
?for OKTA
Overall Risk Meter
Top Failure Risks for OKTA
Okta Profile
Company Name
Okta
Company Website
https://www.okta.com/HQ Location
100 1st St, San Francisco, California 94105, US
Employees
501-1000
Social
Financials
IPO