D2iQ Overview
D2iQ's Enterprise Kubernetes Platform (DKP) simplifies the deployment and management of Kubernetes at scale, transforming the time-consuming process into a swift operation. This platform is designed to help businesses reduce their time to market from months to mere days. DKP is tailored for enterprises looking to efficiently manage their Kubernetes environments, offering a streamlined approach that addresses the complexities of large-scale operations. A standout feature is its ability to handle the intricacies of Kubernetes management, making it an attractive choice for organizations aiming to enhance their operational agility. Trusted by leading brands, D2iQ's platform is a go-to solution for those seeking to optimize their Kubernetes strategy.
Use Cases
Customers recommend Collaboration, Helpdesk Management, Onboarding, as the business use cases that they have been most satisfied with while using D2iQ.
Business Priorities
Improve Consistency and Improve Efficiency are the most popular business priorities that customers and associates have achieved using D2iQ.
D2iQ Use-Cases and Business Priorities: Customer Satisfaction Data
D2iQ's features include Personalization, and Dashboard. and D2iQ support capabilities include 24/7 Support, AI Powered, Chat Support, etc. also D2iQ analytics capabilities include Custom Reports, and Analytics.
D2iQ simplifies building and running Kubernetes at scale. Time to market is reduced from months to days.
Popular Business Setting
for D2iQ
Top Industries
- Financial Services
Popular in
- Enterprise
- Large Enterprise
- Mid Market
D2iQ is popular in Financial Services, and is widely used by Enterprise, Large Enterprise, and Mid Market.
D2iQ Customer wins, Customer success stories, Case studies
Why is D2iQ the best choice for Collaboration?
What solutions does D2iQ provide for Onboarding?
How can D2iQ optimize your Lead Management Workflow?
D2iQ Features
- Low
- Medium
- High
| FEATURE | RATINGS AND REVIEWS |
|---|---|
| AI Powered | Read Reviews (22) |
| Custom Reports | Read Reviews (47) |
| Analytics | Read Reviews (18) |
| CAPABILITIES | RATINGS AND REVIEWS |
|---|---|
| AI Powered | Read Reviews (22) |
| Custom Reports | Read Reviews (47) |
| Analytics | Read Reviews (18) |
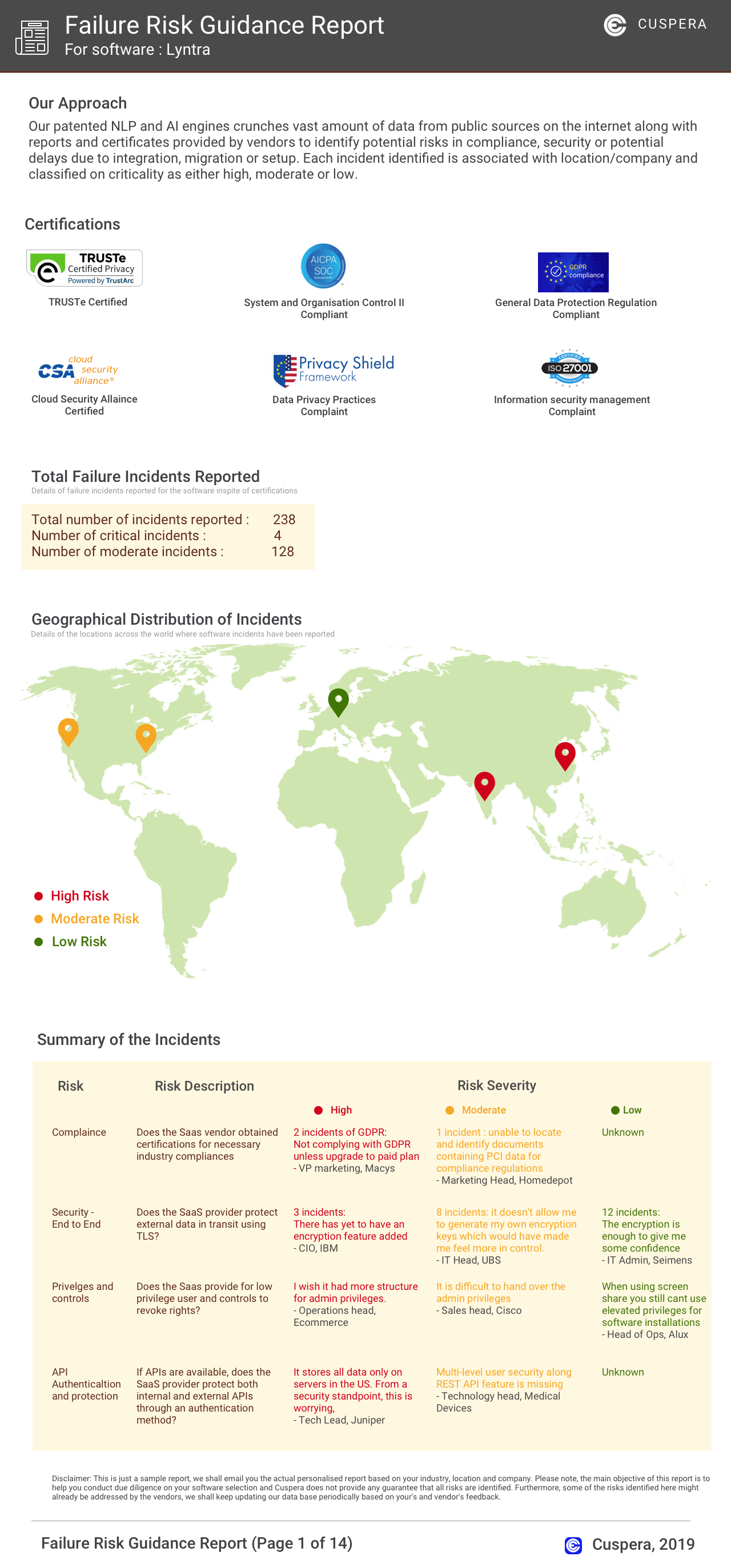
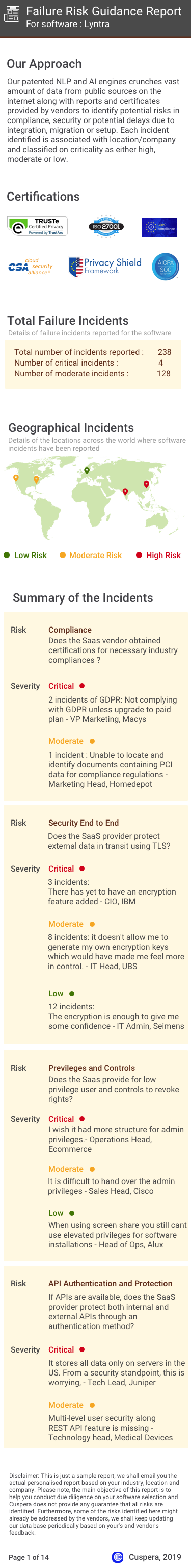
Software Failure Risk Guidance
?for D2iQ
Overall Risk Meter
Top Failure Risks for D2iQ
D2iQ, Inc. News
D2iQ, Inc. Profile
Company Name
D2iQ, Inc.
HQ Location
San Francisco, CA 94104, US
Employees
251-500
Social
Financials
SERIES D